As technology continues to evolve, the ability to seamlessly integrate systems and software has become a key driver of smarter, more efficient operations.
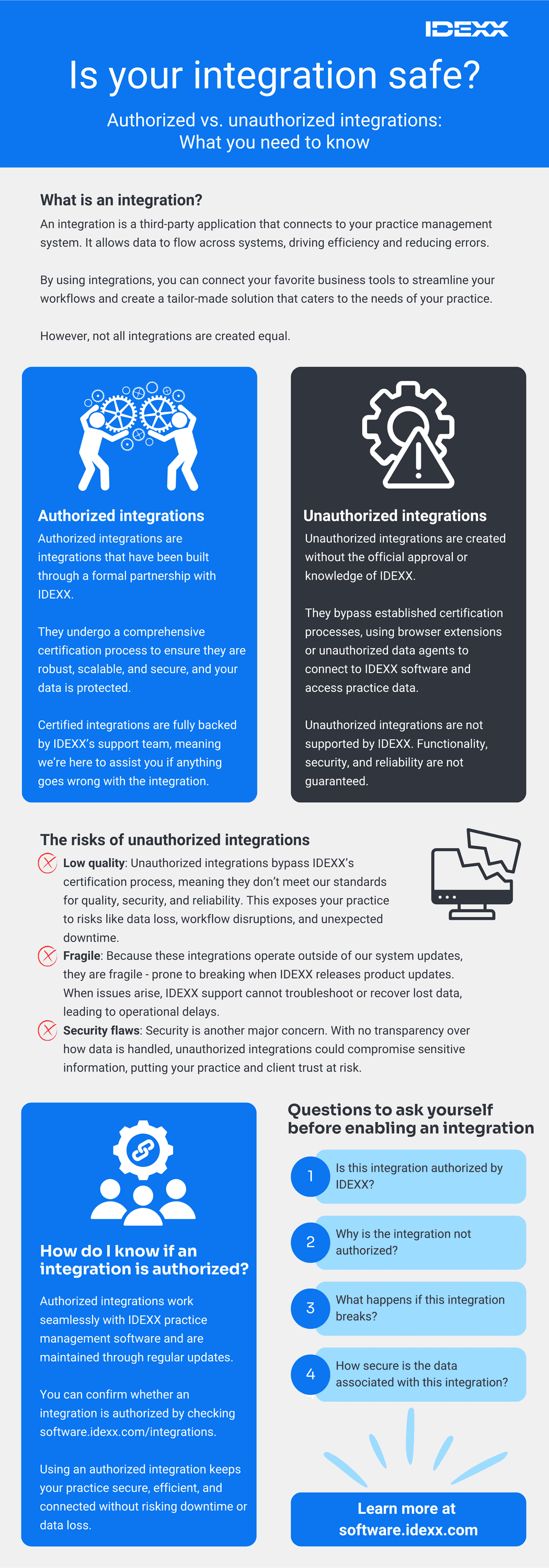
However, not all integrations are created equal. Understanding the difference between authorized and unauthorized integrations is crucial for ensuring the security, functionality, and compliance of your organization's digital ecosystem.
This blog post aims to provide a comprehensive overview of authorized and unauthorized integrations. We’ll explore the benefits of authorized integrations, the dangers associated with unauthorized ones, and offer guidance on how to make informed decisions when integrating new technologies into your workflow.
Key takeaways
- Authorized integrations have been officially approved and vetted by the practice management software provider. These integrations are designed to work effectively with existing systems, providing reliable performance and supportability.
- Unauthorized integrations, while potentially offering quick solutions, can pose significant risks. These risks include security vulnerabilities, system incompatibilities, and potential breaches of compliance regulations.
IDEXX’s integration strategy: partnering with trusted innovators
IDEXX’s integration strategy is simple: We collaborate with companies that share our commitment to innovation, data security, and improving the customer experience. By building a robust ecosystem of trusted integration partners, we empower our users to do business on their own terms.
However, we don’t partner with just anyone.
Each integration partner goes through a rigorous certification process to ensure the partner aligns with IDEXX’s values and technical requirements. What do the partner’s data management processes look like? How does the company handle support queries? In the event of a technical hiccup, can we rely on the partner to resolve the issue?
Our criteria for partnership include:
- Aligned mission: We work with partners who prioritize the same core values, including customer satisfaction, operational efficiency, and data integrity.
- Collaborative support: We maintain close relationships with our partners’ product teams, ensuring any issues can be quickly addressed to minimize disruptions.
- Scalability and reliability: Every certified integration is tested to confirm it can handle real-world veterinary practice demands without compromising performance.
- Data security and compliance: Partners using authorized integrations built to IDEXX’s API library and practices provide those partners credentials to their practice data, enabling the integration. Practices do not need to create ghost users or bots which are not allowed.
By focusing on these standards, we’re able to offer a range of integrations that you can trust to work seamlessly with IDEXX practice management software.
IDEXX is proud to work closely with a broad range of authorized partners to provide a robust and trustworthy integration ecosystem. However, there are some vendors that choose to circumvent our normal integration certification processes.
That might not seem like a big deal. After all, if the software works as advertised, who cares whether IDEXX certified it or not - right?
Unfortunately, it’s not quite that simple. The truth is there are huge differences in terms of functionality, security, and support. Unauthorized integrations can potentially be disruptive to the user experience, compromise sensitive data, and impact functionality of your IDEXX practice management software.
So, when you’re considering integrations for ezyVet, Neo, or Cornerstone, it’s important to understand the difference between authorized and unauthorized solutions.
What are authorized integrations?
Authorized integrations are integrations that have been built through a formal partnership with IDEXX. These integrations undergo a comprehensive certification process to ensure they are robust, scalable, and secure. Certified integrations are understood by IDEXX’s support teams, meaning we can quickly troubleshoot if something goes wrong with the integration.
The following is a high-level overview of the IDEXX certification process:
- Discovery: A vendor applies to be an integrated partner.
- Technical demonstration: A deep dive into the inner works of the integration, where we get a holistic understanding of the vendor's platform, the desired workflows of the proposed integration, and whether IDEXX practice management software’s APIs can adequately support those workflows.
- Contract negotiations: Ensures both IDEXX and the partner understand their responsibilities.
- Sandbox development: Development of the integration in a trial environment.
- Closed beta: Six-week closed beta with select IDEXX customers, including feedback loops.
- Documentation review: Ensure integration documentation is comprehensive and easy for users to understand.
- General release: Once the integration is successfully certified, it can be released to customers.
Importantly, certification isn’t a one-time event. If the partner makes any changes to the way the integration interacts with the IDEXX API, it must be recertified.
What are unauthorized integrations?
Unauthorized integrations are created without IDEXX’s knowledge, consent, or approval. In order to function, these integrations often require the practice to create a “ghost user” or “shadow user” (essentially, a fake user account created in your practice management software). These user types are in breach of IDEXX terms and conditions and can pose a cybersecurity risk as they often are over-permissioned and have ready access to sensitive information. Ghost users can also create infrastructure stress, which can impact other practices. When this occurs, we may need to protect our environment by disabling those ghost users, which can break the unauthorized integration.
Both authorized and unauthorized integrations work by interacting with IDEXX practice management software data structures. But what happens when we make changes to those data structures? When updates are released, we work closely with our authorized integrated partners to ensure a seamless experience for our customers. In contrast, the code of unauthorized integrations is not considered when we update our products, which can result in unexpected issues.
When we say unexpected issues, we’re referring to the very real risk of service interruption or workflow disruption any time your IDEXX practice management software is updated. And because these integrations are implemented without IDEXX’s involvement, IDEXX support teams are unable to troubleshoot the issue, or fix or restore data loss associated with the issue thus impacting your day-to-day operations.
How to verify if an integration is authorized by IDEXX
As a practice owner or manager, you need to be confident that the integrations you use are safe, secure, and fit for purpose.
The simplest way to verify that an integration is officially authorized by IDEXX is to check the IDEXX integrations page. Here, you’ll find the latest list of authorized integrations, which can be filtered by practice management software, type, vendor, and region.
If you can’t see an integration listed on this page, there’s a good chance that it’s unauthorized and potentially unsafe. We strongly recommend not enabling any unauthorized integrations.
If you’re still unsure about the legitimacy of an integration, feel free to reach out to your IDEXX support team. We’ll be happy to confirm whether an integration is authorized and guide you to the best solutions for your practice.
Questions to ask yourself before enabling any integration
Before adding any integration, take a moment to evaluate its credibility and potential risks. Here are some critical questions to ask:
- Is this integration authorized by IDEXX? If it’s not listed on the IDEXX integrations page, it’s probably unauthorized.
- Why is the integration not authorized? It’s possible that the vendor attempted to build an authorized integration but failed to qualify for certification. Or, the vendor may not have even attempted to certify the integration. Why?
- What would happen if this integration breaks? There’s always a risk of failure when using unauthorized integrations. How would your practice handle service disruption or data loss? How would this impact your clients?
- How secure is the data associated with this integration? Unauthorized integrations don’t go through our certification process, leaving you in the dark about how your data accessed and processed. Would you trust an unverified solution with sensitive client and patient information?
Conclusion
Your practice deserves reliable, secure, and scalable solutions that work seamlessly with your IDEXX practice management software.
By choosing authorized integrations, you’re investing in tools that have been vetted and certified by IDEXX. You’re also protecting your data, your system, and your reputation.
Take control of your integrations today and ensure your practice remains efficient, secure, and future proof. Visit the IDEXX integrations page or contact us to learn more about authorized integrations.